Identify vulnerable users before a real attack impacts your bottom line.
While there are tools to help detect and prevent phishing emails from getting to your inbox, hackers are getting more clever and creative and thus are still able to deliver some of those unwanted emails, and they aren't as easy to spot as they once were.
This leaves humans as the last line of defense.
Are you confident that everyone in your organization can spot a phishing email? Many people, including business leaders and even some IT professionals, are falling for
these deceitful scams, so it’s imperative to have the proper training for your entire organization.
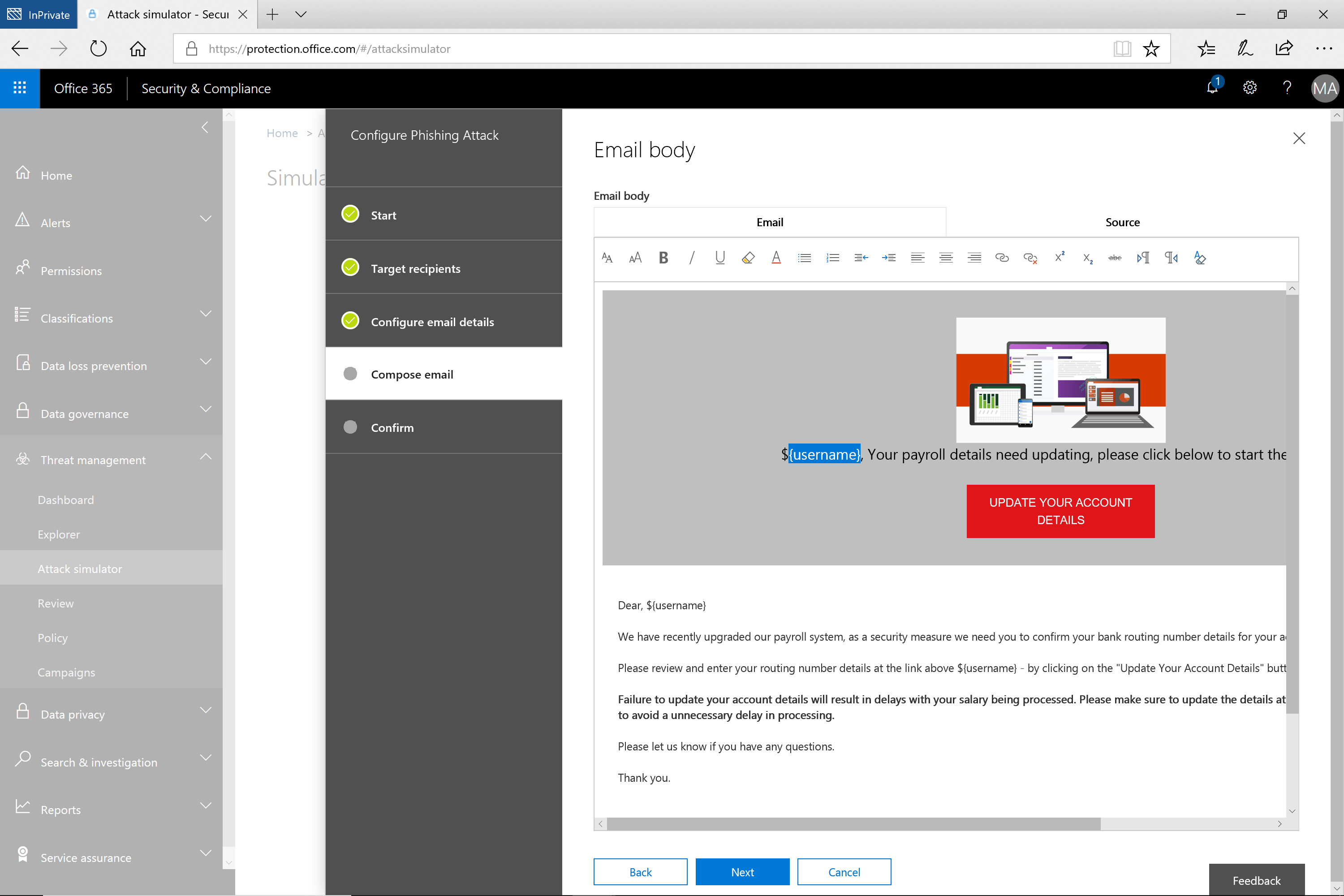
Microsoft Attack Simulator for Office 365 allows Exchange Online users to simulate fake phishing campaigns to test who in your organization may be vulnerable to an attack.
This is a great way to identify potential gaps in your defense and provide an opportunity for training
No matter what type of infrastructure your organization has, your users, your network, and your organization’s data are all
susceptible to socially engineered cyber attacks. It’s critical that in addition to proper training, the training must be tested
through simulated activities to see just how susceptible your users are to this threat.
The Attack Simulator carefully crafts simulated phishing emails based on real data, ensuring the most realistic attack experience. Once the user receives an email, they are directed to a phishing site that mirrors the Office 365 login page.
As with the email message, there are small discrepancies that can alert you to the fact that you are being scammed. Failing to do so will result in the user being flagged in the report generated after the attack is complete. In addition, the user will be taken to a page where they will get information about how to spot phishing attacks, that you can custom create.
The simulated attack tracks the users’ behaviors and reports on their response to these emails, providing invaluable data on how to better secure the organization.
Choose between three kinds of attack simulations: